The Cyber Kill Chain framework developed by Lockheed Martin explains attacker’s progressive steps when attacking a target which can be used to identify and prevent cyber threat.
The Cyber Kill Chain has seven stages as following:
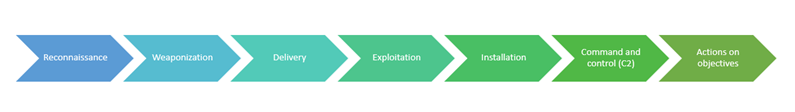
Reconnaissance
This is the initial phase, where the attacker gather’s information about the target. Scanning, Foot printing and Enumeration is done this phase. Information like IP address, Ports & Services, OS, Application, Vulnerabilities etc are discovered.
Weaponization
After gathering data about the target, the attacker builds the weaponised payload which can be malware, ransomware, virus, worm etc that can exploit the vulnerabilities found on the target system.
Delivery
In this phase, the attacker sends the built weaponised payload through email, web, USB etc to the target.
Exploitation
In this phase, the malicious code is executed on the target machine.
Installation
In this phase, the malicious installs itself as a program in the target machine.
Command and control (C2)
In this phase, the attacker takes the remote control of target and starts to command the target by sending instructions.
Actions on objectives
In this phase, the attacker starts working on the objectives which could be stealing/exfiltration of data and bringing the system/service down.
