SQL Injection (SQli) is an attack technique where the attacker exploits the vulnerability in Web Application of not validating inputs and injects malicious SQL statements into the Relative Databases (RDMS).
Web Application is a 3-Tier Architecture. A user accesses the web server and the data from the web server is provided to the application server. The application server processes the data as per user’s request. The application server sends and retrieves data from the database as required to perform the user’s requested task.
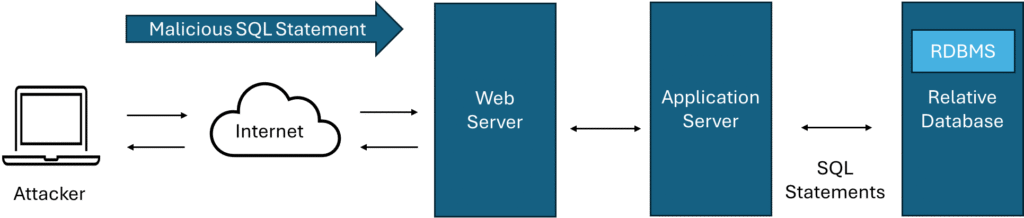
SQL Injection Attack is not a Database Vulnerability rather it’s due to Web Application Vulnerability. Based on the user’s task, the web server sends the commands to the application server. The Application Server processes the commands and sends the required SQL statements to the RDBMS. The Attacker sends malicious SQL statements to the Web Server which in turn gives it to the Application Server. If the Application Server doesn’t validate the SQL statement properly, the malicious statement will be processed by the RDMBS and executed in the Relative Database. If malicious statements are executed successfully, the attacker can get un-authorized data or manipulate data. Web Developers uses Server-Side Scripting languages to develop and build Web Applications. While developing, if the Security Design is not done properly and thus the Applications don’t validate the input SQL statements properly, the SQL Injection happens successfully.
Impact of SQL Injection Attack
Authentication & Authorization Bypass – Authentication bypass is where Attacker bypasses the authentication process and login into applications. In authorization bypass, attacker bypasses the authorization process and gets privilege access.
Data Loss – Attackers can get access to un-authorized data.
Data Integrity Loss – Attackers can manipulate data
Data Availability Loss – Attackers can delete data and make them un-available.
Types of SQL Injection
In-Band SQLi
The same channel is used for SQL injection. This is the most common SQLi attack which is simple and easy to perform. There are two types of In-Band SQL Injection attacks as following:
Error-Based SQLi – The SQLi attack is performed, so that the SQL error is thrown back from which the attacker can understand about the database.
Union-Based SQLi – The SQLi attack uses SQL Union operator that combines multiple SQL statement to get response from database to understand the database.
Inferential SQLi (Blind SQLi)
In an Inferential SQLi, there is no response from the database rather generic message is displayed on the web page. The attacker asks true or false questions and assesses the response from the database. Based on the response, the attacker cracks the database. Inferential SQLi is time-insensitive attack meaning the attack can’t be completed in a definite time. The following are types of Inferential SQLi.
Boolean-based SQLi – The attacker assesses the response of the database for the true or false questions. The variation in the HTTP response from the database is studied and the attacker understands the database.
Time-Based SQLi – The attacker assesses the time taken for the true or false questions. Based on the time taken, the attacker understands the database.
Out-of-band SQLi
In Out-of-band SQLi attack, the attacker uses out of band channel like Email to perform the SQL injection.
Reference
